QTRUST Admin Proxy
Secure Administration of Critical Infrastructures
The QTrust Admin Proxy enables secure remote maintenance of critical internal systems or production facilities by external service providers. Based on the Multilevel Trusted OS PitBull by General Dynamics, the QTrust Admin Proxy acts as a secure terminal or jump server. External or non-company administrators log in for remote maintenance using strong authentication (QTrust ID) and perform system management from there.
Always know who connected to what and when
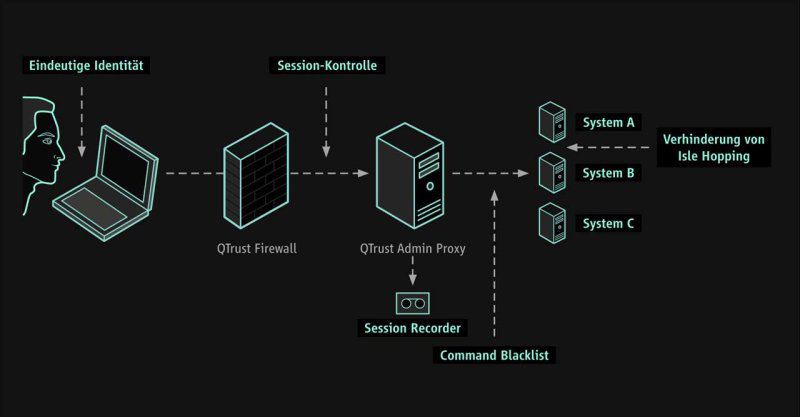
The Multilevel-Security protection (MLS protection) of the QTrust Admin Proxy ensures full control of the session immediately after the first step of verifying the user's identity, preventing the service provider from breaking out of their authorization context. This prevents malware from being introduced into the critical infrastructure and restricts access to unauthorized systems (Isle Hopping), meaning accessing a third-party system through another system, or even data leakage.
An adaptable Command Blacklist prevents the intentional or unintentional execution of unauthorized commands. Central logging and session recording also enable secure monitoring of the service providers' activities.
QTrust Admin Proxy Overview
- Admin PC serves only as a simple ThinClient
- Full desktop/terminal functionality
- Strong authentication (up to three factors with biometrics)
- Central, tamper-proof logging
- Prevention of unauthorized commands (Command Blacklist)
- Prevention of access to unauthorized systems (Isle Hopping)
- Video recording of all activities (optional)
Highlights
- Clear identity of the accessing party and thus clear accountability
- Full session control and individual setting of barriers
- Compromise of the access computer no longer poses a problem
- Prevention of Isle Hopping / jumping to other systems or sections
- Tamper-proof log files in convenient evidence packs
Data and Facts
- Support for all administration protocols such as RDP, SSH, HTTPS, VNC, and more
- Highly secure operating system platform based on PitBull®
- Verification of the identity of (external) administrators (Clear liability boundaries and compliance)
- Process isolation between individual administrators through compartments
- Network isolation between involved network segments through network labels
- Tamper-proof through role separation (ISO 27001 compliant)
- Preventing or documenting sabotage attempts by the administrator
- Escape or hacking resistance to prevent attackers from breaking out of the access context
- Prevention of data leakage via remote administration
- Prevention of intentional or unintentional introduction of malicious code into the infrastructure
- Implementation of military security strategies
